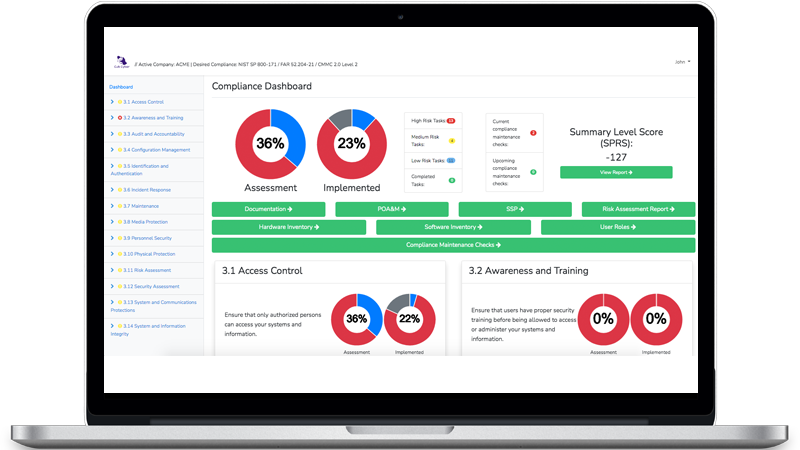
Review User Privileges and Access Rights
One of the most basic principles of cybersecurity is the “principle of least privilege”. The principle of least privileges states that users and programs should only have the necessary privileges to complete their tasks. Another important concept is “need-to-know”. Users should only have access to the information and data they have a “need-to-know” for.
The idea is that the fewer privileges an account has and the less data/information it has access to, the less damage a hacker or insider threat can do with the account.
I see so many organizations not following the principle of least privilege. Don’t be one of them. Review your user accounts and privileged security groups to see which users have more privileges than needed. Revoke privileges and group memberships as necessary.
Before revoking permissions or privileges, coordinate with the management to ensure that employees have enough privileges and permissions to complete their work.
Uninstall non-essential software
If you conduct an inventory of the software installed on your end-points and servers you might be surprised at what you find. Spotify, Apple Music, Steam, and other non-essential software are all liable to show up. If you don’t need the software to support your organization's mission then uninstall it. Why? Because of the “principle of least functionality”.
The principle of least functionality requires that systems are configured to provide only essential capabilities and to prohibit or restrict the use of non-essential functions. This includes non-essential software. The less software you have on your servers and end-points the smaller your attack surface and the easier it is to maintain your systems.
Start by creating a software whitelist consisting of mission essential software. From there start uninstalling whatever isn’t on the whitelist. Add software to your whitelist as necessary. You want to enforce your whitelist using a technical control so that only whitelisted software runs on your systems.
Revoke Admin Rights from Non-Privileged Users
Why do employees who only use their browser and Microsoft Office to complete their work have local administrator rights on their computer? In general, a user does not need local admin rights on their workstation, if they do then confirm it with their manager. Otherwise revoke local admin rights from non-privileged users.
By revoking local admin rights you are mitigating 94% of windows vulnerabilities.
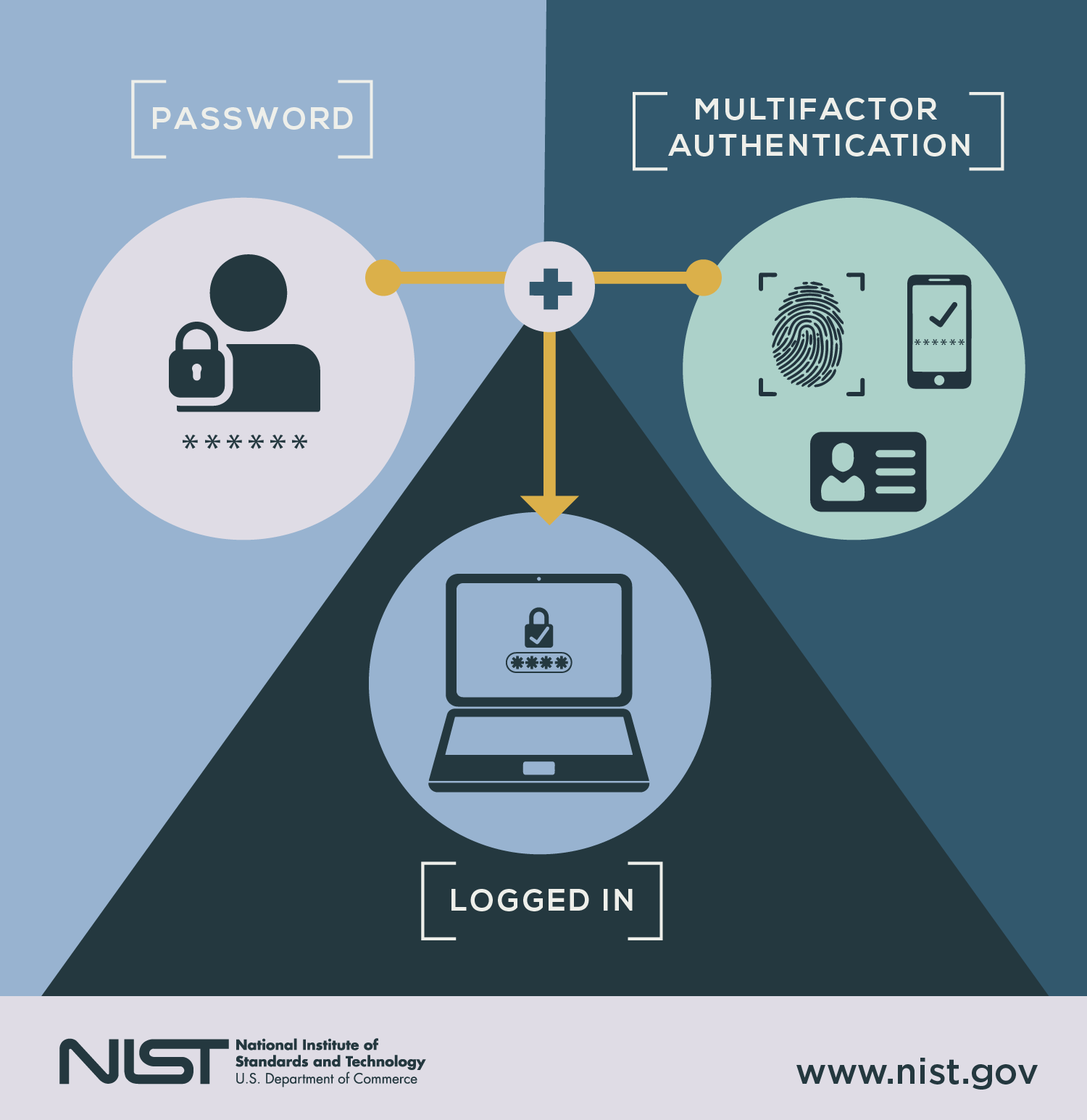
Turn on Multi-Factor Authentication for Cloud Resources
If an account is used to log into a cloud application then it needs to be protected by multi-factor authentication. Most cloud resources allow you to do this. The last thing you need is a high-profile employee falling for a phishing attack and then having his/her Office 365 account hacked. By turning on MFA for all your cloud accounts you reduce the probability of that scenario from occurring.
Encrypt Portable Storage Devices and Mobile Devices
If you have portable storage devices (USB flash drives and external HDD or SSD drives), laptops, tablets, and smartphones they need to be encrypted. This is because they can be transported out of your secure facility. If the device is lost or stolen and isn’t encrypted, anyone can access the data on the device.
Make sure to use FIPS validated cryptography when encrypting digital media.