
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-2-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-2-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-2-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-2-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-1-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-1-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-1-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 4-1-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 3-1-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 3-1-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 3-1-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 3-1-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-9-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-9-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-9-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-9-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-8-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-8-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-8-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-8-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-7-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-7-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-7-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-7-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-6-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-6-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-6-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-6-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-5-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-5-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-5-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-5-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-4-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-4-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-4-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-4-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-3-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-3-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-3-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-3-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-2-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-2-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-2-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-2-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-15-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-15-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-15-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-15-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-14-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-14-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-14-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-14-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-13-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-13-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-13-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-13-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-12-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-12-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-12-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-12-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-11-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-11-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-11-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-11-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-10-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-10-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-10-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-10-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-6
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-5
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 2-1-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-6
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-5
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-9-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-8-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-8-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-8-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-7-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-7-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-6-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-6-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-6-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-6-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-5-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-5-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-5-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-5-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-4-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-4-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-3-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-3-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-3-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-3-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-2-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-2-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-2-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-10-5
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-10-4
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-10-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-10-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-10-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-1-3
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-1-2
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet Essential Cybersecurity Controls (ECC – 2 : 2024) - Control - 1-1-1
Practical guide for SMBs to implement Essential Cybersecurity Controls (ECC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SI.L2-3.14.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - SI.L1-B.1.XIV
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - SI.L1-B.1.XIII
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - SI.L1-B.1.XII
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.9
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.8
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.16
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.15
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.14
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.12
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.11
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.10
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - SC.L2-3.13.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - SC.L1-B.1.XI
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - RA.L2-3.11.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - RA.L2-3.11.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - RA.L2-3.11.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PS.L2-3.9.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PS.L2-3.9.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PE.L2-3.10.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PE.L2-3.10.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PE.L2-3.10.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PE.L2-3.10.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - PE.L2-3.10.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - PE.L1-B.1.VIII
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - PE.L1-B.1.IX
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.9
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.8
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MP.L2-3.8.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - MP.L1-B.1.VII
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - MA.L2-3.7.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IR.L2-3.6.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IR.L2-3.6.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IR.L2-3.6.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.9
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.8
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.11
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.10
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - IA.L2-3.5.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - IA.L1-B.1.VI
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - IA.L1-B.1.V
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.9
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.8
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CM.L2-3.4.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CA.L2-3.12.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CA.L2-3.12.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CA.L2-3.12.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - CA.L2-3.12.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.9
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.8
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.7
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.6
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.5
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.4
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AU.L2-3.3.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AT.L2-3.2.3
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AT.L2-3.2.2
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AT.L2-3.2.1
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.22
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.21
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.20
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.19
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.13
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet NIST SP 800-171 REV.2 / CMMC 2.0 Level 2 - Control - AC.L2-3.1.12
Practical guide for SMBs to implement NIST SP 800-171 REV.2...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - AC.L1-B.1.IV
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - AC.L1-B.1.III
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - AC.L1-B.1.II
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →
How to Meet FAR 52.204-21 / CMMC 2.0 Level 1 - Control - AC.L1-B.1.I
Practical guide for SMBs to implement FAR 52.204-21 / CMMC...
Read more →

How to Implement HIPAA Facility Access Controls (164.310(a)(1)): A Step-by-Step Compliance Guide
A practical, step-by-step guide to implementing HIPAA Facility Access Controls...
Read more →
How to Draft ISO 27001-Compliant Confidentiality and NDA Templates (Control 6.6 / Code 282)
Step-by-step guidance to create Compliance Framework-aligned confidentiality and NDA templates...
Read more →
How to Create Audit-Ready HIPAA 164.316(a) Policies and Procedures: Templates, Documentation, and Change Control
Step-by-step guidance for building audit-ready HIPAA 164.316(a) policies and procedures...
Read more →
How to Create and Maintain Written HIPAA Policies and Procedures (164.316(b)(1)) — Practical Implementation Checklist
Step-by-step guidance for creating, documenting, and maintaining HIPAA-compliant written policies...
Read more →
How to Create an Audit-Ready Log Review Policy for CMMC - AU.L2-3.3.3 with Templates and Checklists
Step-by-step guidance to build an audit-ready log review policy for...
Read more →
How to Configure Multi‑Factor Authentication and Account Controls to Satisfy FAR 52.204-21
Practical, step‑by‑step guidance for small contractors to configure multi‑factor authentication...
Read more →
How to Build an ISO 27001-Compliant Source Code Access Policy: Templates and Implementation Steps
Step-by-step guidance and ready-to-use templates to build a source code...
Read more →
How to Achieve ISO 27001 Compliance for Policies in 30 Days: Rapid Implementation Checklist and Sample Policy Pack
Practical 30-day plan to build ISO 27001-aligned policies, a sample...
Read more →

CMMC Phased Rollout Begins: What Defense Contractors Need to Know Now
The CMMC phased implementation has officially started. Learn critical dates,...
Read more →

CMMC Level 1: How to Implement Visitor Escort and Monitoring to Meet PE.L1-B.1.IX
Learn exactly how small businesses can implement visitor escort and...
Read more →
Quarterly Access Reviews That Work: Verifying Authorized Users and Devices for AC.L1-B.1.I (CMMC Level 1)
Learn how to run no-nonsense quarterly access reviews to verify...
Read more →
How to Identify Role-Specific Risks and Turn Them into Targeted Modules for NIST 800-171 3.2.1
Learn how to map role-specific risks into targeted training modules...
Read more →











How to Meet AC.L2-3.1.7
Practical guide for SMBs to implement AC.L2-3.1.7 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.6
Practical guide for SMBs to implement AC.L2-3.1.6 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.5
Practical guide for SMBs to implement AC.L2-3.1.5 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.4
Practical guide for SMBs to implement AC.L2-3.1.4 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.3
Practical guide for SMBs to implement AC.L2-3.1.3 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.2
Practical guide for SMBs to implement AC.L2-3.1.2 using Microsoft 365...
Read more →
How to Meet AC.L2-3.1.1
Practical guide for SMBs to implement AC.L2-3.1.1 using Microsoft 365...
Read more →
How to Configure SSO and MFA for AC.L2-3.1.1 in Microsoft Entra ID (Azure AD), Okta, and Google Workspace
Learn how to meet AC.L2-3.1.1—limit system access to authorized users,...
Read more →
Configure IAM (SSO, MFA, RBAC) to Limit Access to Authorized Users for AC.L2-3.1.1 Compliance
Learn how to configure SSO, MFA, and RBAC to meet...
Read more →
From Reception to Audit: Real-World Implementation Tips for Escorting Visitors under NIST SP 800-171
Step-by-step, practical guidance for implementing visitor escorting controls to meet...
Read more →
Meeting CMMC Level 1 Requirement | AC.L1-B.1.III – EXTERNAL CONNECTIONS [FCI DATA]
How Small Businesses Can Meet It.
Read more →
Meeting CMMC Level 1 Access Control - AC.L1-B.1.I – Limiting System Access to Authorized Users, Processes, and Devices
Learn how to meet CMMC Level 1 Access Control -...
Read more →
Meeting CMMC AC.L2-3.1.4 - Separation of Duties
Learn how to meet CMMC AC.L2-3.1.4 - Separation of Duties...
Read more →
14+ Security Settings to Boost WhatsApp Privacy
Configure these settings to combat stalkers, spammers, and everyone else...
Read more →
How to Get Your Smartphone Ready for the Next Disaster
If configured correctly, during a disaster a smartphone can be...
Read more →
DeepSeek AI Database Leaked Secret Keys & Over 1 Million Log Lines
DeepSeek AI database security flaw uncovers confidential keys, chat records,...
Read more →
Russian hacker group Star Blizzard launch spear phishing attack via WhatsApp
The Russian hacker group Star Blizzard posed as U.S. government...
Read more →
Biden executive order imposes new cybersecurity standards for companies that do business with the U.S. government
The Biden administration aims to enhance digital security for both...
Read more →
How to Perform a CMMC Level 1 Self-Assessment
Learn how to perform a CMMC Level 1 Self-Assessment
Read more →
Telegram Hands Over Thousands Of Users Data To US Law Enforcement
The arrest of the Telegram founder seems to have caused...
Read more →
Volkswagen data leak exposes location of 800,000 electric car drivers
A Volkswagen subsidiary data breach has exposed the location and...
Read more →
US Army soldier arrested for hacking President Donald Trump’s calls
US Army soldier shared on the Telegram messaging service that...
Read more →
US Treasury documents stolen by Chinese Hackers in Major Incident
Hackers supported by the Chinese government successfully penetrated the Treasury...
Read more →
NIST SP 800-171 Rev 3 or Rev 2? Which is Required in 2024?
What are the new NIST SP 800-171 requiremets? Do they...
Read more →
Ensure that between two and four global admins are designated - Microsoft 365
Designate between two and four global administrators to ensure effective...
Read more →
Establish two emergency access accounts for critical situations, ensuring continuity and security in your system - Microsoft 365
Secure your Microsoft 365 environment by ensuring administrative accounts are...
Read more →
Ensure that administrative accounts are distinct and solely cloud-based - Microsoft 365
Secure your Microsoft 365 environment by ensuring administrative accounts are...
Read more →
4 Business Benefits of Implementing ISO 27001
ISO 27001 is well known in the information security field....
Read more →
How To Conduct An ISO 27001 Risk Assessment
Implementing ISO 27001 involves conducting thorough information security risk assessments,...
Read more →

BYOD - Do employees care about data security?
According to a survey conducted by Kaspersky Labs, only 10%...
Read more →
Oakwood Hospital Worker Fired For Facebook Comments in HIPAA Violation
Michigan healthcare provider, Oakwood Healthcare, Inc., has verified that an...
Read more →
HIPAA for Managed Service Providers
Understanding HIPAA is crucial for Managed Service Providers offering services...
Read more →
4 Stages of Containing a Data Breach
Data breaches have become increasingly common, leading many organizations to...
Read more →
ISO 27001 Asset Based Risk Assessment
For those who are new to information security risk assessments,...
Read more →

5 Reasons Why Your Business Needs a Pen Test
Penetration testing is a highly effective method for evaluating your...
Read more →
ISO 27001 Internal Audit
Accelerating the ISO 27001 audit process can be facilitated by...
Read more →
ISO 27001 and Third Party Vendors
Organizations pursuing ISO 27001 certification but rely on third-party vendors...
Read more →

HIPAA Password Sharing
Password sharing in healthcare may contribute to productivity in certain...
Read more →
Evidence Remotley Wiped From Police Station
Placing phones in a microwave prevents hacking?
Read more →
How ISO 27001 Can Protect Homeland Security
ISO 27001 can address the US Department of Homeland Security’s...
Read more →


Why ISO 27001 Information Classification Is Important
The classification of information plays a crucial role in every...
Read more →
ISO 27001 Benefits for Small Organizations
Many small organizations believe that implementing ISO 27001 is either...
Read more →

HIPAA Compliance for Medical Centers
Medical centers must comply with the Administrative Simplification standards of...
Read more →
HIPAA Compliance In Urgent Care
The correlation between HIPAA compliance in urgent care is not...
Read more →
HIPAA Compliance Officer
To become HIPAA compliant, a Covered Entity or Business Associate...
Read more →
HIPAA Email Compliance
Covered entities and business associates are obligated to implement various...
Read more →
HIPAA Compliant Hosting
In order to safeguard sensitive patient information stored in the...
Read more →
HIPAA Text message (SMS) Regulations
Text message (SMS) regulations under HIPAA outline the specific circumstances...
Read more →

HIPAA Training Requirements
The HIPAA training requirements lean more towards offering guidance rather...
Read more →

HIPAA and HITECH
Covered Entities and Business Associates must familiarize themselves with the...
Read more →
HIPAA Password Sharing Policy
A Password Sharing Policy that is compliant with HIPAA should...
Read more →
HIPAA Compliance for Medical Records
Safeguarding the security of medical records are required to meet...
Read more →
HIPAA Risk Assessment
Performing a HIPAA risk assessment is crucial for ensuring compliance...
Read more →
HIPAA Guide for Dentists
The master guide for HIPAA compliance for all dentists, regardless...
Read more →
HIPAA Encryption Requirements
Everything you need to know about HIPAA encryption requirements
Read more →

HIPAA Telemedicine
The comprehensive HIPAA guide for telemedicine and the proper methods...
Read more →
HIPAA Social Media Policy
Healthcare organizations must prioritize HIPAA compliance when it comes to...
Read more →
Healthcare Cybersecurity
An In-depth Look at Cybersecurity in the US Healthcare Industry...
Read more →
UnitedHealthcare Pays Settlement for HIPAA violation over Patient Medical Records Request
UnitedHealthcare Settles for $80,000
Read more →
Incident Response Testing for NIST SP 800-171 & CMMC 2.0
Use our incident response tests to meet requirement 3.6.3.
Read more →
Control and Manage Physical Access Devices – NIST SP 800-171 & CMMC 2.0
How do you meet the security requirement 3.10.5 “Control and...
Read more →
Is Your Microsoft 365 Tenant Configured for NIST SP 800-171 & CMMC Compliance?
More than likely, you haven’t configured your Microsoft 365 tenant...
Read more →
Flying to the Cloud – IT & Security Transformation
Learn how we configured a client's Microsoft 365 environment to...
Read more →
Maintaining Systems and Compliance
Learn how our Azure AD services can streamline and secure...
Read more →
Data Mining and Extracting Historical Data
How we helped a regional logistics company access historical data...
Read more →
Email marketing automation platform = six figure increase in sales
How we helped a small business increase their sales by...
Read more →
Certification after Certification
Learn how our policies and procedures service enabled a customer...
Read more →
Small Business, Big Compliance - NIST SP 800-171
Learn how we helped a DoD contractor meet DFARS NIST...
Read more →
The Physics Behind Microsoft 365 Security
Learn how we helped a DoD contractor meet compliance requirements...
Read more →
Security Configuration Settings for NIST SP 800-171 & CMMC Compliance
Learn how to meet your configuration management requirements for NIST...
Read more →
How to Meet NIST SP 800-171 & CMMC Mobile Code Requirements
Learn how to meet your mobile code protection requirements for...
Read more →
Looking for an Information Security Framework? Use this.
Using a security frame helps an organization establish and meet...
Read more →
Guide to NIST SP 800-171 & CMMC 2.0 Security Control Domains
Learn the objectives of each security control family.
Read more →
Using BitLocker Encryption for NIST SP 800-171 & CMMC 2.0 Compliance
Learn how to use BitLocker encryption to meet NIST SP...
Read more →
Guide to Insider Threat Awareness Training for NIST SP 800-171 & CMMC
Learn how to meet insider threat training requirements for NIST...
Read more →
Guide to Split Tunneling (3.13.7) for NIST SP 800-171 and CMMC
What is split tunneling and how does it relate to...
Read more →
The Ultimate Guide to Privacy and Security Notices for NIST 800-171 and CMMC
What is a privacy and security notice? Where does it...
Read more →
The Ultimate Guide to Incident Response for NIST 800-171 and CMMC 2.0
How do you meet NIST 800-171 and CMMC 2.0 incident...
Read more →
The Ultimate Guide to USB Compliance for CMMC and NIST 800-171
Can I still use USB storage if we implement NIST...
Read more →
Cyberwarfare vs Cyber Espionage, What is the Difference?
Cyber buzzwords always get thrown around causing confusion for readers....
Read more →
Top 5 In Demand Cybersecurity Certifications
Which of these top 5 cybersecurity certifications do you have?...
Read more →
Data Classification Labels for Your Small Business
Having trouble with data classification in your small business? Here...
Read more →
10 Ways to Improve Your Small Business's Cybersecurity
Perform these tasks to greatly improve cybersecurity at a small...
Read more →
NIST SP 800-171 Personnel Security Requirements
Learn everything you need to know about your Personnel Security...
Read more →
What is a System Security Officer, System Owner, and Information Owner?
Learn what these essential roles are for your system security...
Read more →
NIST SP 800-171 Physical Security Requirements Explained
Learn how to meet your NIST SP 800-171 and CMMC...
Read more →
Vulnerability Scanning Requirements for NIST SP 800-171
Learn how to meet your NIST SP 800-171 and CMMC...
Read more →
How I Passed the CISSP Exam on My First Try
Follow my tips on how to pass the CISSP exam....
Read more →
NIST SP 800-171 Least Privilege Requirements
What does “Least Privilege” mean and what are the associated...
Read more →
NIST SP 800-171 Separation of Duties Requirements
What does “Separation of Duties” mean and what are the...
Read more →
How the Time on your Computer Affects NIST SP 800-171 Compliance
There are many intricate requirements related to NIST SP 800-171...
Read more →
System Security Plans Explained
To meet NIST SP 800-171 requirements you must create and...
Read more →
NIST SP 800-171 CUI Sanitization and Destruction Methods
Learn how to meet your NIST SP 800-171 media sanitization...
Read more →
What Documentation Should You Have for NIST SP 800-171?
A cybersecurity program isn’t really a formal program until it...
Read more →
What are the NIST SP 800-171 Password Requirements?
The password requirements for NIST SP 800-171 are not very...
Read more →
What CMMC 2.0 Means for your Business
CMMC 2.0 has streamlined CMMC and brought it in line...
Read more →
Easy to Use Incident Response Checklist
Organizations should have standardized procedures for responding to incidents, use...
Read more →
How to Protect the Confidentiality of CUI
Learn how to protect the confidentiality of CUI using physical...
Read more →
Using DISA STIGs to Meet NIST SP 800-171 and CMMC Requirements
Learn how using DISA STIGs can help you meet your...
Read more →
How to Create a Hardware and Software Inventory for your System Security Plan
Every system security plan should include or reference a hardware...
Read more →
How to Meet Requirements 3.6.3 and IR.3.099: Test the organizational incident response capability.
Learn how to “Test the organizational incident response capability” to...
Read more →
What are NIST SP 800-171 and CMMC Malicious Code Protection Requirements?
In this post, we will discuss how to meet your...
Read more →
How to Create a Plan of Action & Milestones for NIST SP 800-171
A plan of action and milestones document is critical to...
Read more →
What is a Collaborative Computing Device?
Learn what a collaborative computing device is and how to...
Read more →
What is a Basic (Contractor Self-Assessment) NIST SP 800-171 DoD Assessment?
Learn what a basic NIST SP 800-171 DoD assessment is...
Read more →
How to Meet NIST SP 800-171 & CMMC Personnel Security Requirements
To meet CMMC and NIST SP 800-171 requirements, organizations must...
Read more →
How to Meet NIST SP 800-171 & CMMC Physical Protection Requirements
To meet CMMC and NIST SP 800-171 requirements, organizations must...
Read more →
Meeting Personnel Training Requirements for NIST SP 800-171 & CMMC Using Free Resources
The NIST 800-171 and CMMC security frameworks both have an...
Read more →
What is a Summary Level Score (SPRS)? + How to Calculate it
Read more →
Meeting AC.1.001 and 3.1.1 Security Control Requirements for CMMC & NIST SP 800-171
Read more →
How to Control and Monitor Mobile Code for NIST SP 800-171 & CMMC
Read more →
NIST SP 800-171: How to Perform a Self-Assessment
Read more →
Digital Bug Out Bag Essentials
Are you preparing for a natural disaster, civil unrest, nuclear...
Read more →
Cybersecurity Border Crossing and Travel Tips
When traveling or crossing through border controls there are a...
Read more →
Easy to Follow Online Privacy Guide
Learn how to clean up your online presence and stay...
Read more →
Data Classification 101 Guide
Classifying and labeling data is a critical part of any...
Read more →
Is it Cybersecurity or Cyber Security? How do you spell it?
Is cybersecurity spelled as one word or two? The answer...
Read more →
The Principle of Least Functionality, Simplicity is the Ultimate Sophistication
Employing the principle of least functionality is critical for organizations...
Read more →.png)
Information Security or Cyber Security? Which term should we use?
The term cyber security is often heard in the media,...
Read more →
The History of Hacking: 1903 the world's first Hack
In 1903 the world’s first hacking incident occurred, marking the...
Read more →
CMMC: Policies and Procedures Contractors Should Have
Companies with cybersecurity maturity model certification (CMMC) level two or...
Read more →
5 Open-source Cybersecurity Tools Every Company Needs
Using free and open-source software (FOSS) to meet your cybersecurity...
Read more →
6 Cybersecurity Risks Associated with Working From Home
Although an operational necessity, allowing employees to work from home...
Read more →
CMMC Portable/Removable Storage Security Requirements
What are the cybersecurity maturity model certification (CMMC) requirements for...
Read more →
Laptops given to British school kids came preloaded with malware
Laptops supplied to British schools by the Department for Education...
Read more →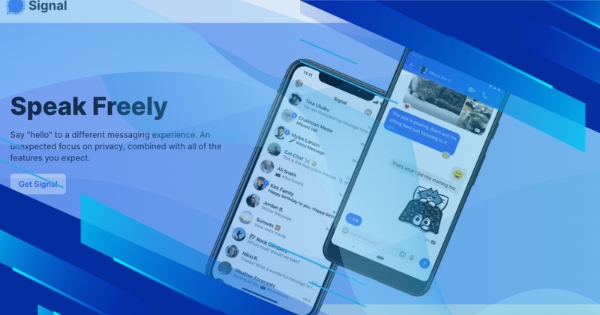
12 Things You Need to Know About the Signal Messenger App
The Signal Messenger App is rising in popularity. Here are...
Read more →
5 Simple Ways to Improve Your Organization’s Cybersecurity
Tackling cybersecurity challenges is no walk in the park. However,...
Read more →
CMMC FAQ
Cybersecurity Maturity Model Certification (CMMC) frequently asked questions (FAQ)
Read more →
Signs an Employee Might Be an Insider Threat
More than 34% of businesses around the globe are affected...
Read more →
Why Ad Blockers Should Be Part of Your Endpoint Security Strategy
Malvertising is a serious threat that can often be overlooked....
Read more →
How to Protect Printers From Cyber Threats
We are used to locking down workstations and servers however...
Read more →
How Going Paperless Improves Cybersecurity
Want to help save the environment and improve your information...
Read more →
4 Reasons Small Business Doesn't Invest in Cybersecurity
Small businesses are often the target of cyber attacks. Why...
Read more →
3 Free Ways to Boost Cybersecurity Awareness
Training employees on cybersecurity practices and reminding them of security...
Read more →
Should You Punish Employees for Cybersecurity Violations?
Everyone can agree that breaking the rules should have its...
Read more →
Physical Security Measures are an Important Part of Cybersecurity
Our data may be stored digitally but fundamentally it is...
Read more →
What is Split Tunneling? Should You Allow It?
What is split tunneling as it relates to virtual private...
Read more →

CMMC Privacy & Security Notice Requirements
Learn which companies need to deploy system use notifications, what...
Read more →
What You Need to Know About the Cybersecurity Maturity Model Certification (CMMC)
There are important new updates to the DoD Cybersecurity Maturity...
Read more →
What are Your CMMC Antivirus Requirements?
Companies with CMMC requirements will need to deploy antivirus software...
Read more →
5 Free Apps & Services To Protect Your Privacy
Tired of Silicon Valley and the Government tracking your every...
Read more →
Practical Home Cybersecurity Tips
Use these tips to protect your home from cyber threats....
Read more →
How Often Should Users Be Required to Reset Their Password?
Does requiring users to reset their passwords every few months...
Read more →
What is the difference between "Separation of Duties" and "Least Privilege"
Separating the duties of employees and implementing the principle of...
Read more →
What is the Difference Between Data Privacy and Security?
Privacy and security are related but what is the difference?...
Read more →
FALSE: Hiding your WiFi SSID is more secure than not, and here's why:
Does hiding your SSID improve security?
Read more →

How to Create A Business Impact Analysis (BIA)
We discuss business impact analysis definition, steps, and provide templates...
Read more →
How to Choose an Enterprise Grade Multi-factor Authentication (MFA) Solution
Knowing how to choose the right multi-factor authentication (MFA) solution...
Read more →
Cheat Sheets Every Cybersecurity Pro Needs
Check out these useful cheat sheets for cybersecurity tools like...
Read more →
What are keyloggers and what guidance does the CMMC provide
A keylogger is a device or application that is used...
Read more →
What is an Incident Response Plan? What Should it Contain?
The occurrence of a cybersecurity incident isn’t a matter of...
Read more →
What information should you collect when a cybersecurity incident occurs? What are your CMMC Incident Response Requirements?
It is important for organization’s to collect information on cybersecurity...
Read more →
What is the NIST Privacy Framework?
The NIST Privacy Framework provides organizations with a tool to...
Read more →
Use This Simple Trick to Prevent 94% of Windows Vulnerabilities
By revoking administrator rights from a Windows system you can...
Read more →
How a Gap Analysis Can Help Your Company Prepare for CMMC
By conducting a third party CMMC gap analysis your company...
Read more →
14 year old boy takes down Amazon, CNN, Yahoo!, and eBay. Also CMMC and DDoS Attacks...
A 14 year old boy took down Amazon, CNN, Yahoo!,...
Read more →
What is Dumpster Diving and how does it relate to the cybersecurity maturity model certification (CMMC)?
In the world of cybersecurity, dumpster diving is a technique...
Read more →
CMMC - What is CUI, CDI, CTI, and FCI
What is CUI, CDI, CTI, and FCI? CMMC (Cybersecurity Maturity...
Read more →
What is Encryption and how is Encryption used in the CMMC (Cybersecurity Maturity Model Certification)?
Encryption is the process of encoding information so that it...
Read more →
What is a Firewall? How do they relate to the Cybersecurity Maturity Model Certification (CMMC)?
A firewall is a network security system that monitors and...
Read more →

What's the Difference Between SSL and TLS?
In short, SSL is the now deprecated predecessor of TLS....
Read more →

Practicing Good OpSec on Social Media
Social media can help you connect with friends and family,...
Read more →
Building a Patch and Vulnerability Management Program
A patch and vulnerability management program is one of the...
Read more →
Common CMMC Misconceptions
Many defense contractors are confused about CMMC. Here are two...
Read more →
Why Your Company Needs to Block Browser Extensions
Browser extensions can increase productivity, however, left unmanaged they can...
Read more →

How to Provide Free Cybersecurity Training to Your Employees
Your employees can receive some of the same training as...
Read more →
How to Protect Your Smartphone from Hackers
Continue reading to find out how to prevent hackers from...
Read more →
How to Protect Your Twitter Account From Hackers
Learn to how to secure your twitter account to avoid...
Read more →
7 Small Business Cybersecurity Statistics You Need to Know
Here are the top small business cybersecurity statistics you need...
Read more →
Successful Cybersecurity Programs Focus on the Basics
Companies often overlook the basic elements of cybersecurity, leaving them...
Read more →
Top 10 Useful Cybersecurity Statistics for 2020
Here are the top 10 recent cybersecurity statistics you need...
Read more →
How to Control Portable Storage Devices
77 percent of corporate end-users surveyed have used personal flash...
Read more →
How to Create a System Security Plan (SSP)
A system security plan (SSP) lists an organization’s cybersecurity requirements...
Read more →
Use DISA STIGs to Secure Your IT Systems
The Defense Information Systems Agency (DISA) has a wide range...
Read more →
New CMMC Timeline - What Your Company Needs to Do Now
The cybersecurity maturity model certification accreditation board (CMMC-AB) released a...
Read more →
How to Sanitize or Destroy Digital & Non-Digital Media
Did you know that 42% of used drives sold on...
Read more →
You Company’s Culture Must Adapt to CMMC
A company culture fostering discipline will be a great asset...
Read more →
How to Create an IT Acceptable Use Policy + Templates
Creating an acceptable use policy for your information system is...
Read more →
Change Control - Important Considerations Before Making Changes to your IT Systems
Change control procedures are the backbone of any mature cybersecurity...
Read more →
CMMC - What is meant by Mobile Code?
When reading the term “Mobile code” many folks are left...
Read more →
What is an information system?
Understanding what an information system is and its components is...
Read more →
America Needs the Cybersecurity Maturity Model Certification (CMMC) Program
“From U.S. businesses to the federal government, to state and...
Read more →
What are your CMMC password requirements?
We explain your cybersecurity maturity model certification (CMMC) password requirements....
Read more →
CMMC Audit & Accountability Domain Explained
In this post we explain the CMMC audit & accountability...
Read more →
CMMC Access Control Domain Explained
In this post we explain the CMMC access control domain...
Read more →

Does your company need a CMMC?
Around 300,000 companies will need to earn a cybersecurity maturity...
Read more →
America's Plan to Protect its Defense Industry from Cyber Threats
America will protect its defense industrial base from cyber attacks...
Read more →



What is the Cybersecurity Maturity Model Certification (CMMC)?
The cybersecurity maturity model certification is a new DoD cybersecurity...
Read more →

Do CMMC requirements apply to non-DoD contracts?
As of June 2020, CMMC requirements will only apply to...
Read more →

Who Needs a CMMC Certification?
Learn which companies need to earn a CMMC certification to...
Read more →
CMMC - What is Federal Contract Information (FCI)?
Learn what Federal Contract Information (FCI) is and how it...
Read more →
CMMC - What is controlled unclassified information (CUI)?
Learn what CUI is and how it relates to CMMC....
Read more →


CMMC - What Companies Struggle with the Most
Here are the top cybersecurity compliance requirements DoD contractors struggle...
Read more →