NIST Privacy Framework Summary
The NIST Privacy Framework is a tool organizations can leverage to identify and manage privacy risks. It was developed by the National Institute of Standards and Technology. The framework can be used by both the public and private sectors alike. It is not technology or law specific. The framework includes security controls and recommendations organizations may choose to follow. By using the NIST privacy framework organizations can identify and map systems and data. Identify important business processes, personnel, and the systems supporting them. Via the framework organizations can also conduct a privacy risk assessment as well as manage risks from the data processing ecosystem. Organizations can also establish governance policies and manage awareness and training. Organizations can also create policies and processes to implement privacy requirements. The NIST privacy framework also has familiar security controls from NIST SP 800-53 that can help organizations maintain data privacy.
NIST Privacy Framework Structure
The NIST Privacy Framework has three principal components. They are the core, profiles, and implementation tiers.
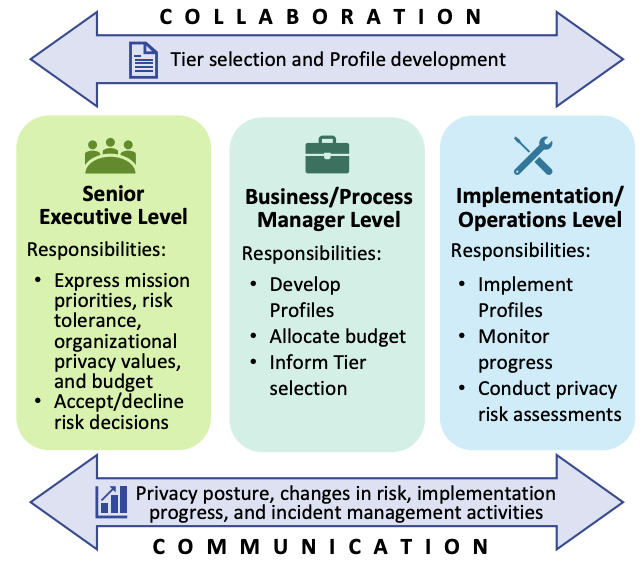
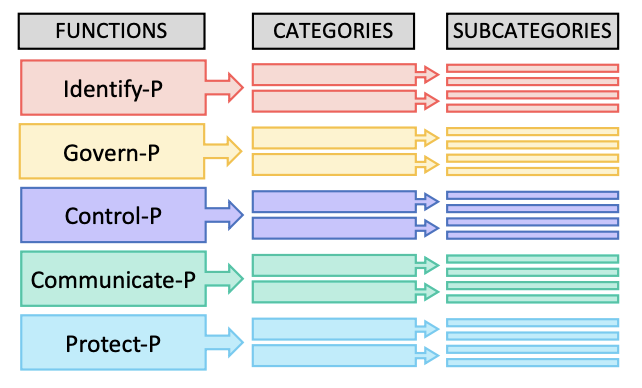
The Core: The Core is a set of privacy protection activities and outcomes that allows for communicating prioritized privacy protection activities and outcomes across an organization from the executive level to the implementation/operations level. The Core is further divided into key Categories and Subcategories—which are discrete outcomes—for each Function.
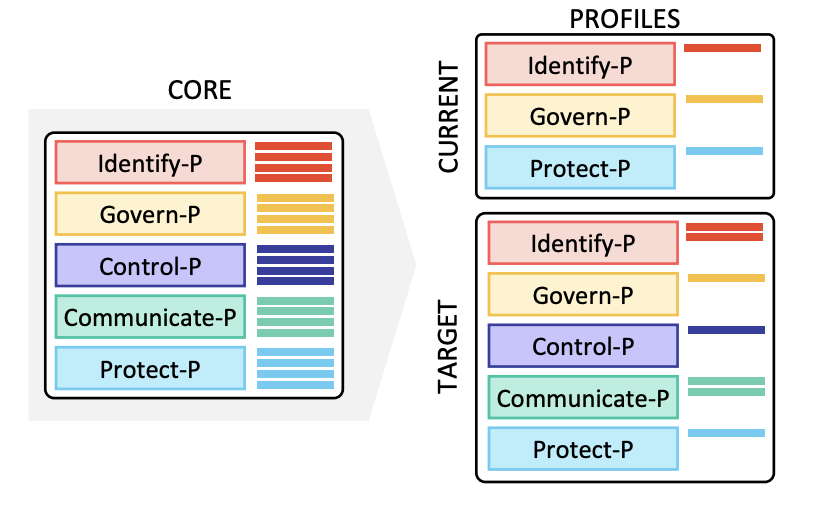
Profiles: Profiles are a selection of specific Functions, Categories, and Subcategories from the
Core that an organization has prioritized to help it manage privacy risk. There are two types of profiles. One is the current profile and the other is the target profile. The current profile is an organization’s “as is” state, and the target is what the organization would like to achieve.
Implementation Tiers: Implementation tiers provide a point of reference on how an organization views privacy risk and whether it has sufficient processes and resources in place to manage that risk. There are four NIST privacy framework implementation tiers. The four tiers are Tier 1 Partial, Tier 2: Risk Informed, Tier 3: Repeatable, and Tier 4: Adaptive. Organizations can select which tier they would like to achieve. The higher the tier the more mature the organization’s privacy is.
How to Implement the NIST Privacy Framework?
Organization’s seeking to implement the NIST Privacy Framework should first review the NIST Privacy Controls to determine their current privacy profile. Next they should create a target profile, that is the controls they would like to implement. The NIST Privacy Framework does not tell companies how to specifically implement any controls so it is upto your organization to determine how to implement them. As stated previously, some of the NIST Privacy Framework’s controls are pulled from NIST SP 800-53 making other guidance from NIST a good resource for companies seeking to implement the NIST Privacy Framework. If your organization needs help implementing the NIST privacy framework then reach out to us at info@lakeridge.io.
What are the NIST Privacy Controls?
The NIST Privacy Framework is made up of functions, categories, and subcategories. They can be found in this
linked PDF document.