In NIST SP 800-171 and CMMC 2.0 Level 2 an entire security control family is dedicated to incident response. We will provide an in-depth explanation of incident response and how it relates to your compliance.
Before we discuss incident response, we need to define what an incident is, but perhaps just as important what an incident is not.
What is an Incident?
According to the
NIST glossary, an incident is “an occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.”
Examples of an incident include unauthorized persons accessing secure areas of your facility, malware installed on your computer, a denial-of-service attack targeting your system, and an employee storing sensitive work files on their private computer.
Not everything is an incident, people may often mistake common events for an incident. According to the
NIST glossary, an event is “something that occurs within a system or network.” An example of an event is your syslog server reaching full disk capacity and not being able to accept more logs. This is not an incident, rather an event.
Distinguishing an event from an incident is important because an incident requires you to activate your incident response plan. This can involve informing the U.S. Department of Defense of an incident along with creating incident reports. So, it is important to use good judgement when trying to determine if something is an event or an incident. The key difference is that events don’t jeopardize confidentiality, integrity, or availability and they do not violate security policies.
What is Incident Response?
According to the
NIST glossary, the definition of incident response is “The mitigation of violations of security policies and recommended practices.”
NIST Special Publication SP 800-61 Rev. 2 “Computer Security Incident Handling Guide” is the go-to source for incident response, especially concerning NIST SP 800-171 and CMMC. To understand what incident response is, we will take you through the incident response lifecycle mentioned in NIST SP 800-61 Rev.2.
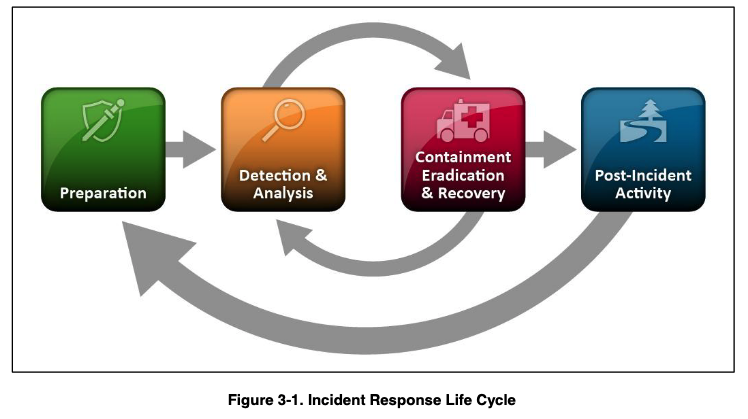
The Incident Response Life Cycle
Preparation:
The preparation phase of incident response involves establishing your incident response capability. This includes putting together an
incident response plan and incident response team. It also involves training incident response personnel. Preparation also includes securing and maintaining your systems to prevent incidents from occurring. You should also put together an
incident response checklist.
Detection and Analysis:
Detection involves trying to identify incidents. This can be accomplished by receiving alerts from anti-malware software installed on your systems, alerts from network intrusion detection systems, SIEM alerts, reviewing system logs, reviewing publicly available information on vulnerabilities, and receiving reports from your organization’s personnel.
Analysis involves documenting incidents (e.g., collecting logs and notes) and prioritizing them by categorizing incidents. Prioritization involves determining the impact of an incident, this helps determine the response towards the incident.
This phase also involves notifying the appropriate persons and organizations that an incident has occurred. According to DFARS 252.204-7012, “when the Contractor discovers a cyber incident that affects a covered contractor information system or the covered defense information residing therein, or that affects the contractor’s ability to perform the requirements of the contract that are designated as operationally critical support and identified in the contract... Rapidly report cyber incidents to DoD at
https://dibnet.dod.mil.”
Containment:
Containment involves preventing an incident from causing increased damage. An example of containment is disconnecting a computer infected with malware from the network. It is important not to accidentally destroy any evidence when containing an incident. You should generally take a disk image of a computer infected with malware and collect any logs associated with the incident.
Eradication and Recovery
Eradication involves eliminating components of an incident such as deleting malware, disabling breached user accounts, and mitigating vulnerabilities. In recovery, you are bringing the systems that were affected by the incident back to normal operation. It is a good idea to have backups of your data and systems to help simplify the recovery process.
Post-Incident Activity
After an incident occurs, you should identify lessons learned. What caused the incident and what changes can be made to prevent recurrence. Was the response to the incident adequate? What improvements can be made to the incident response? These types of questions should be discussed amongst the incident response team. You should also determine how long you will retain evidence related to incidents.
Incident Response Requirements for NIST SP 800-171 and CMMC 2.0 Level 2
There are three security controls that create incident response requirements for NIST 800-171 and CMMC 2.0 level two, they are 3.6.1, 3.6.2, and 3.6.3. How do you meet these requirements?.
3.6.1: Establish an operational incident-handling capability for organizational systems that includes preparation, detection, analysis, containment, recovery, and user response activities.
This
requirement means that your organization needs to have an incident response team and incident response plan covering the incident response life cycle we just discussed. An incident response plan template is available within the
Compliance Accelerator app. As far as creating an incident response team, you may use members of your organization to form the team. You should include a person from executive management and IT staff. If you don’t have IT staff, include tech savvy employees but be sure to train them in incident response. You can alternatively outsource this service.
3.6.2: Track, document, and report incidents to designated officials and/or authorities both internal and external to the organization.
This
requirement means that you need to keep an incident report for all your incidents and report the incidents to the appropriate persons and organizations. If the incident involves controlled unclassified information you need to report it to the Department of Defense at
https://dibnet.dod.mil.
This requirement also includes “tracking and documenting incidents” which involves capturing evidence about an incident and tracking incidents in something like an issue tracker. Be sure to have disk imaging tools available to collect evidence and have spare drives to store audit logs and system images related to incidents.
3.6.3: Test the organizational incident response capability.
This
requirement means that you need to test your incident response plan and incident response team. This requirement can be met by holding table-top incident response exercises. The center for internet security has table-top exercises you can use. Make sure to document the exercises and their results and make adjustments to your incident response capability as required.
3.6.3: Test the organizational incident response capability.
With the right documentation, testing, and attentiveness you can meet your NIST SP 800-171 and CMMC 2.0 incident response requirements. To find out if you are meeting them and your other requirements use Compliance Accelerator. You can also download your incident response template and incident report form from the app.
Conclusion
With the right documentation, testing, and attentiveness you can meet your NIST SP 800-171 and CMMC 2.0 incident response requirements. To find out if you are meeting them and your other requirements use This
Compliance Accelerator. You can also download your incident response template and incident report form from the app.