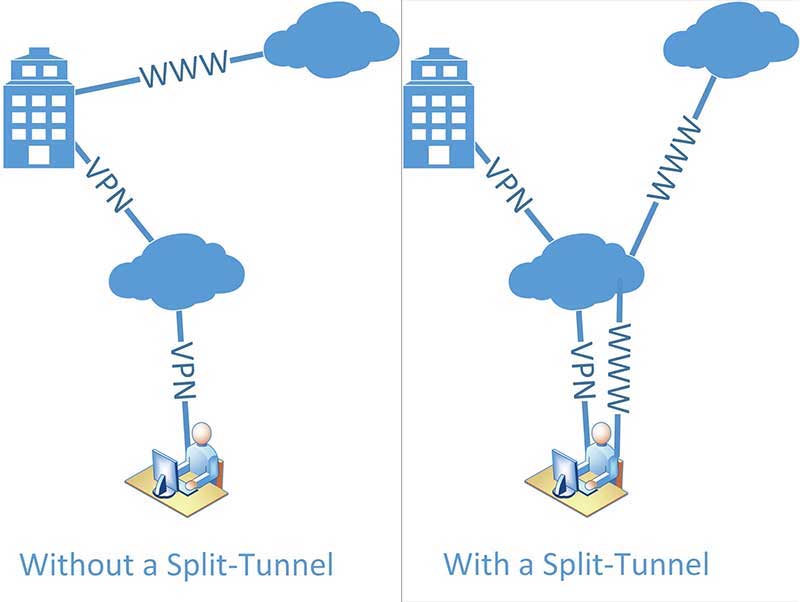
What is Split Tunneling?
Split Tunneling is a VPN setting that allows a VPN user to route a portion of their internet traffic through an encrypted virtual private network while routing the rest through a separate tunnel on the open network.
Split tunneling allows you to access resources on a corporate network via the VPN by routing that connection through an encrypted tunnel while internet traffic is not routed through that tunnel.
Benefits of Split Tunneling
Split tunneling reduces traffic on corporate networks, because not all of a remote user’s traffic goes through the VPN connection. This results in increased speed through reduced latency. Split tunneling also provides privacy benefits to VPN users because their internet traffic isn’t being monitored and logged by their company.
Disadvantages of Split Tunneling
From a security perspective allowing split tunneling creates additional risk. When split tunneling is enabled the firewall rules that apply to computers on your internal network won’t apply to your remote endpoints. If you have certain protocols and websites blocked in your firewall settings these won’t apply to your remote end-points. Basically any perimeter defense you have setup for your network won’t apply to your remote end-points.
Should You Use Split Tunneling?
It depends. If speed, convenience, and a lower internet bill is important for your organization then enabling split tunneling is a good option for you. You can make up for some of the security risks by improving the security of your endpoints by leveraging the firewall on your end points and using other tools such as Cisco’s OpenDNS.
If security is paramount to your organization then you should disable split tunneling. This provides you more control over your end-points and can help you meet cybersecurity compliance requirements.
Split Tunneling CMMC Requirements
CMMC Practice SC.3.184 states: Prevent remote devices from simultaneously establishing non-remote connections with organizational systems and communicating via some other connection to resources in external networks (i.e., split tunneling).
It is clear that if you have cybersecurity maturity model certification (CMMC) requirements and use a VPN you need to disable split tunneling.