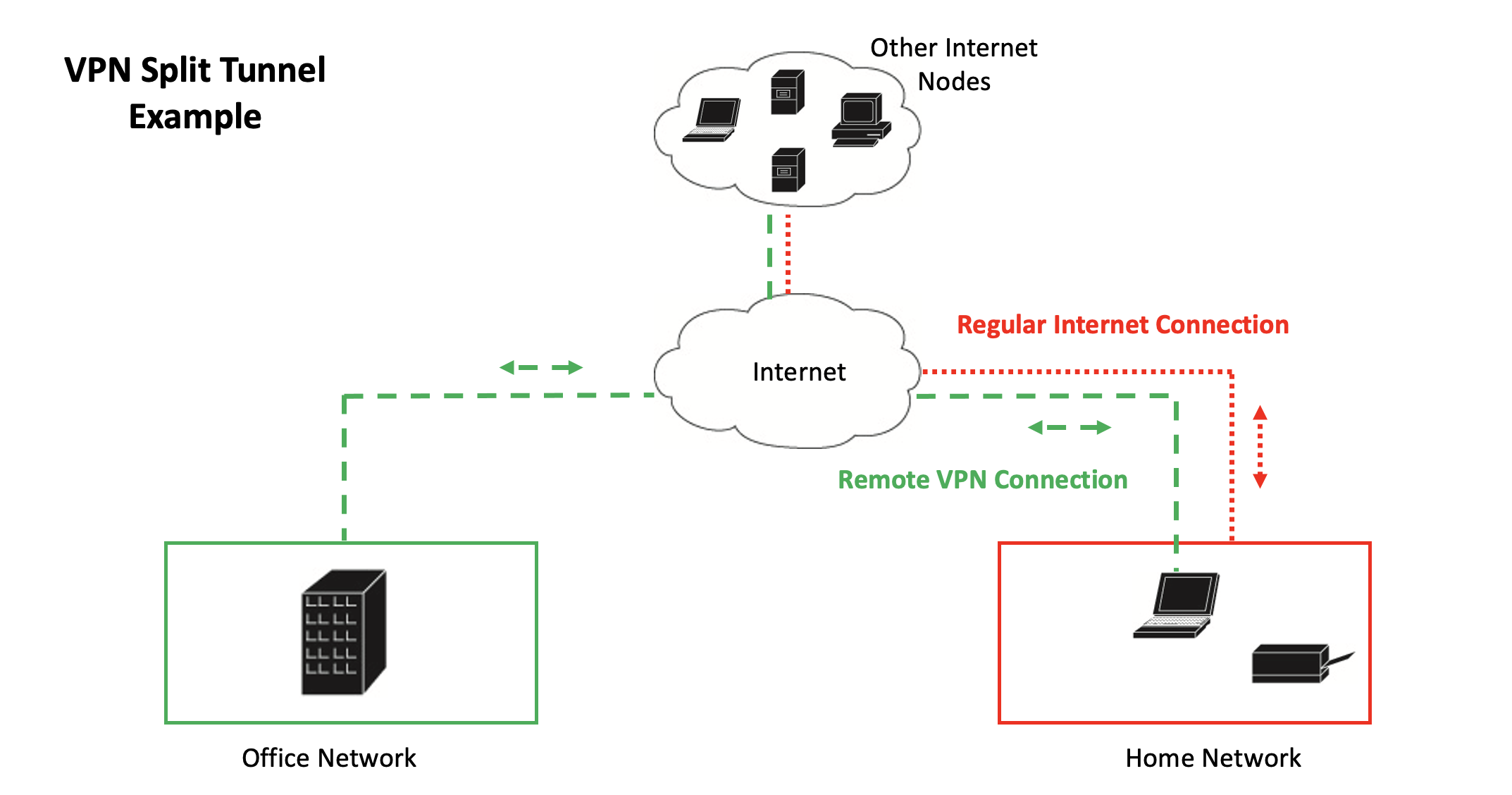
What is Split Tunneling?
When discussing split tunneling, we are discussing a virtual private network (VPN) setting. When discussing virtual private networks (VPN)s within the context of NIST SP 800-171 and CMMC we are not talking about personal VPNs like Nord VPN. We are talking about VPNs configured by an organization to allow users remote access to their organization’s systems on-premises resources such as file or SharePoint servers.
According to the
NIST glossary, split tunneling is “A method that routes organization-specific traffic through the SSL VPN tunnel, but routes other traffic through the remote user's default gateway.”
The benefits an organization gains by allowing
split tunneling is that there is less load on their VPN infrastructure because only the user’s traffic that is accessing the remote network is processed through the VPN. Other traffic like watching YouTube or accessing cloud resources is routed through the user's own network directly to the internet. The benefit here is faster connection speeds for the user and less load on the VPN infrastructure which means reduced IT costs.
Split tunneling allows a user to access their organization’s on-premises resources (e.g., a file server) via the VPN while also allowing the user to access their own network resources (e.g., the printer on their home network).
NIST SP 800-171 and CMMC: Disable Split Tunneling
NIST SP 800-171 and CMMC 2.0 control 3.13.7 requires that you “Prevent remote devices from simultaneously establishing non-remote connections with the information system and communicating via some other connection to resources in external networks.”
In plain English this means that you need to disable split tunneling for your VPN connections. You need to check with the support documentation for your VPN appliance/service to determine how to disable split tunneling for your system.
What is the issue with split tunneling?
According to
NIST SP 800-53, Split tunneling in effect allows unauthorized external connections, making the system more vulnerable to attack and to exfiltration of organizational information.