What is Mobile Code?
According to the National Institute of Science and Technology (NIST), mobile code is a software program or part of a program obtained from remote systems, transmitted across a network, and executed on a local system without explicit installation or execution by the recipient.
Mobile code is not an application you install on a computer. Mobile code isn’t an application you install on your phone. Mobile code is a program that is generally provided to you by a server over the internet that runs on your computer. You are not required to install the program rather it runs on your computer in an application such as your internet browser.
Have you ever tried to complete an online training course and it asks you to make sure that Java on your computer is updated to the latest version? That is because the online training course is provided to you via a Java program. Java programs are an example of “mobile code”.
NIST SP 800-171 & CMMC Mobile Code Requirement
Under the “System and Communications Protection” domain, security control 3.13.13 requires that organization’s “control and monitor the use of mobile code.”
How to Meet Mobile Code Requirements
How you meet this requirement generally depends on your environment. Most of our customers use Windows computers and have a Microsoft 365 environment, so we will assume you do as well for this guide.
The easiest way to meet your mobile code control requirements is to simply implement the Windows 10 Microsoft Baseline Security Configuration and Microsoft Edge Baseline using Microsoft Endpoint Manager. These configuration policies include security settings restricting mobile code like Java and ActiveX.
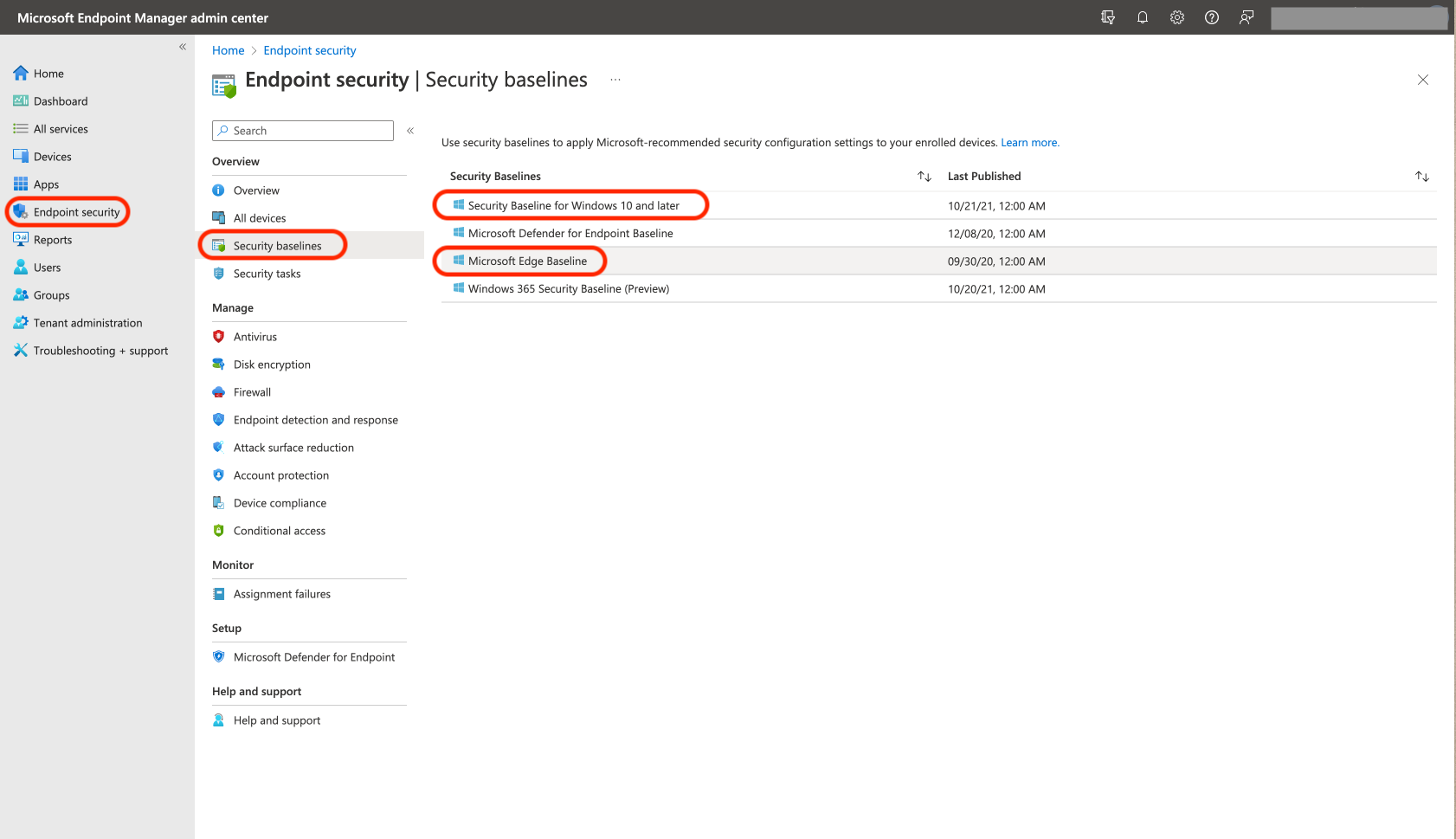
To implement these settings in Endpoint Manager simply go to “Endpoint security”, then “Security baselines”, then select the “Security Baseline for Windows 1 and later” baseline and apply it to your Windows 10 computers. Repeat this for the “Microsoft Edge Baseline”.
If you are still using group policy, you can follow the Windows 10 DISA STIG to implement your mobile code related security requirements.