Failing to properly sanitize or destroy digital and non-digital media can result in the loss of your organization’s sensitive data. Here is how to do it the right way.
Types of Media:
There are two types of media. Digital and non-digital. Digital media includes hard drives, USB thumb drives, CDs, floppy disks, and tape drives. Non-digital media generally includes paper and microfilm.
S
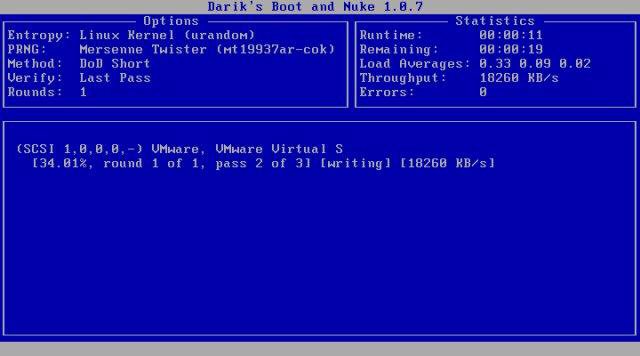
Methods for sanitizing and destroying digital media
Clearing: uses software or hardware products to overwrite user addressable storage space on the media with non-sensitive data, using the standard read and write commands for the device.
Purging: methods include overwrite, block erase, and Cryptographic Erase, through the use of dedicated, standardized device sanitize commands that apply media-specific techniques to bypass the abstraction inherent in typical read and write commands.
Destroying: methods include disintegration, pulverization, melting, and incineration. The application of physical destruction techniques may be the only option when the media fails and other Clear or Purge techniques cannot be effectively applied to the media, or when the verification of Clear or Purge methods fails (for known or unknown reasons).
Methods for destroying non-digital media
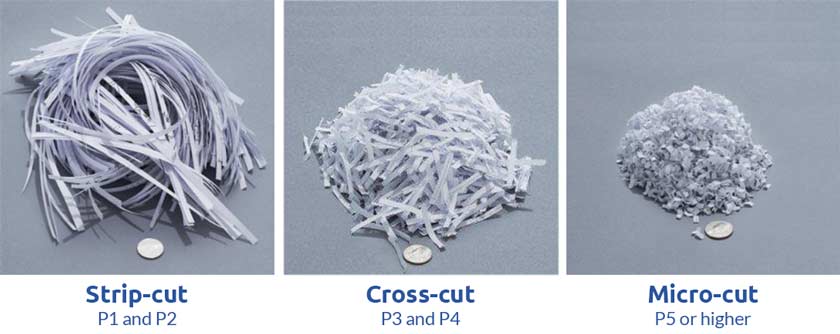
Shredding: Destroy paper using cross-cut shredders which produce particles that are 1 mm x 5 mm (0.04 in. x 0.2 in.) in size (or smaller), or pulverize/disintegrate paper materials using disintegrator devices equipped with a 3/32 in. (2.4 mm) security screen.
Shredding paper properly is critical, the below image demonstrates the results of various shredding methods.
As you can see, paper that is not properly shredded can be reconstructed and read.
Burning: Destroy microforms (microfilm, microfiche, or other reduced image photo negatives) by burning.
Between former President Obama and Vice President Biden you can see a stripped burn bag. Any documents placed in the bag are to be burned until they turn to white ash.
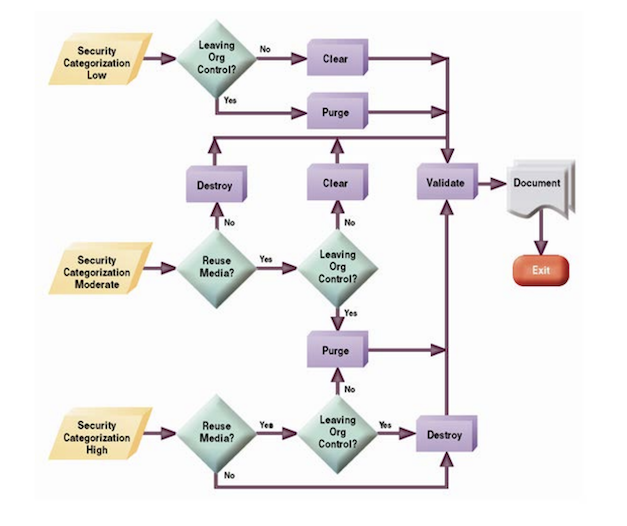
Which sanitiation or destruction method should you use?
If you are going to reuse a device within your organization you do not need to completely destroy the device. The method used for destroying your media is dependent on where the media will go and the security categorization of the data stored on the media. The below diagram is quite useful.
Documenting the sanitation or destruction of media
You should document the destruction of media in a “certification of sanitation”
(download our template). If you paid a third party to destroy your media (e.g., hard disk shredding) then you should receive documentation from them verifying that your media has in fact been destroyed.
Data Sanitation Software
Referenced Resources