What is FIPS 140-2?
Created by the National Institute of Standards and Technology, the Federal Information Processing Standards Publication (FIPS) 140-2, “Security Requirements for Cryptographic Modules”, specifies the requirements an cryptographic algorithm must meet to be used to protect sensitive information on computer systems.
Why Was FIPS 140-2 Created?
The U.S. government needed to ensure that the encryption algorithms it was using were capable of protecting sensitive information. FIPS 140-2 listed requirements that cryptographers needed to meet to have their algorithms validated by the Cryptographic Module Validation Program (CVMP). Under FIPS 140-2, encryption algorithms can be validated at four different security levels.
What are the FIPS 140-2 Levels?
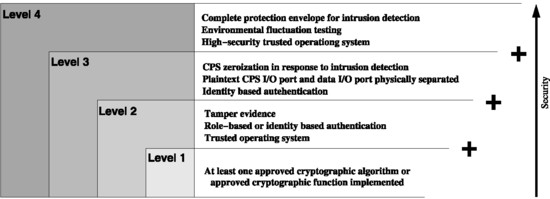
FIPS 140-2 has four levels of security: Level 1, Level 2, Level 3, and Level 4. The higher the level the more secure the more security is provided. FIPS 140-2 specifies the differences between these levels in depth however the below image provides a good overview.
What are the FIPS 140-2 Requirements?
FIPS 140-2 security requirements encompass eleven areas. These areas include the following:
- 1. Cryptographic Module Specification
- 2. Cryptographic Module Ports and Interfaces
- 3. Roles, Services, and Authentication
- 4. Finite State Model
- 5. Physical Security
- 6. Operational Environment
- 7. Cryptographic Key Management
- 8. Electromagnetic Interference/Electromagnetic Compatibility (EMI/EMC)
- 10. Design Assurance
- 11. Mitigation of Other Attacks
Common FIPS 140-2 Compliant Algorithms
- Advanced Encryption Standard (AES)
- Triple-DES Encryption Algorithm (TDEA)
- Digital Signature Standard (DSS)
- Secure Hash Standard (SHS) (SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224 and SHA-512/256)
- HMAC
- SHA-3
What is the Cryptographic Module Validation Program (CMVP)?
The CVMP is available to any vendors who seek to have their products certified for use by the U.S. Government and regulated industries (such as financial and health-care institutions) that collect, store, transfer, share and disseminate "sensitive, but not classified" information. Vendors seeking certification for their products have the tests completed by accredited third-party laboratories.
Modules that have passed these tests can be found in the CVMP database.
FIPS 140-2 to be Replaced by FIPS 140-3
Testing of cryptographic modules against FIPS 140-2 will end on September 22, 2021 and will be replaced by FIPS 140-3.
FIPS 140-2 Validated Cryptography CMMC
With CMMC anything that needs to be encrypted including both data at rest and in transit should be encrypted using FIPS validated encryption alogorithms. If you are seeking a CMMC level 3 or higher certification then this is certainly the case (see
CMMC practice SC.3.177)
Sources